Azure MS SQL Database is an intelligent, scalable, and relational database service built for the cloud. It can automate your database management and maintenance, including routine updates, backups, and security, enabling you to focus on working with your data.
You can ingest data from your Azure MS SQL database using Hevo Pipelines and replicate it to a Destination of your choice.
Prerequisites
-
The MS SQL Server version is 2008 or higher.
-
Hevo’s IP address(es) for your region is added to the Azure SQL Server database IP Allowlist.
-
CHANGE TRACKING and ALTER DATABASE privileges are granted to the database user.
-
SELECT and VIEW CHANGE TRACKING privileges are granted to the database user.
-
Database hostname and port number of the Source instance are available.
Perform the following steps to configure your Azure MS SQL Source:
Create a Geo-Replication Database (Optional)
Geo-Replication is an Azure SQL database feature that allows you to create a readable secondary database in the same region or different regions.
Note: Creation of geo-replication database incurs additional costs.
To use an existing, active geo-replication database or connect Hevo to your master database, skip to Add Hevo IP Addresses to your Database Allowlist section.
To create a geo-replication database:
-
Log in to the Azure Portal.
-
Under Resources, select the database for which you want to create a geo-replication database.
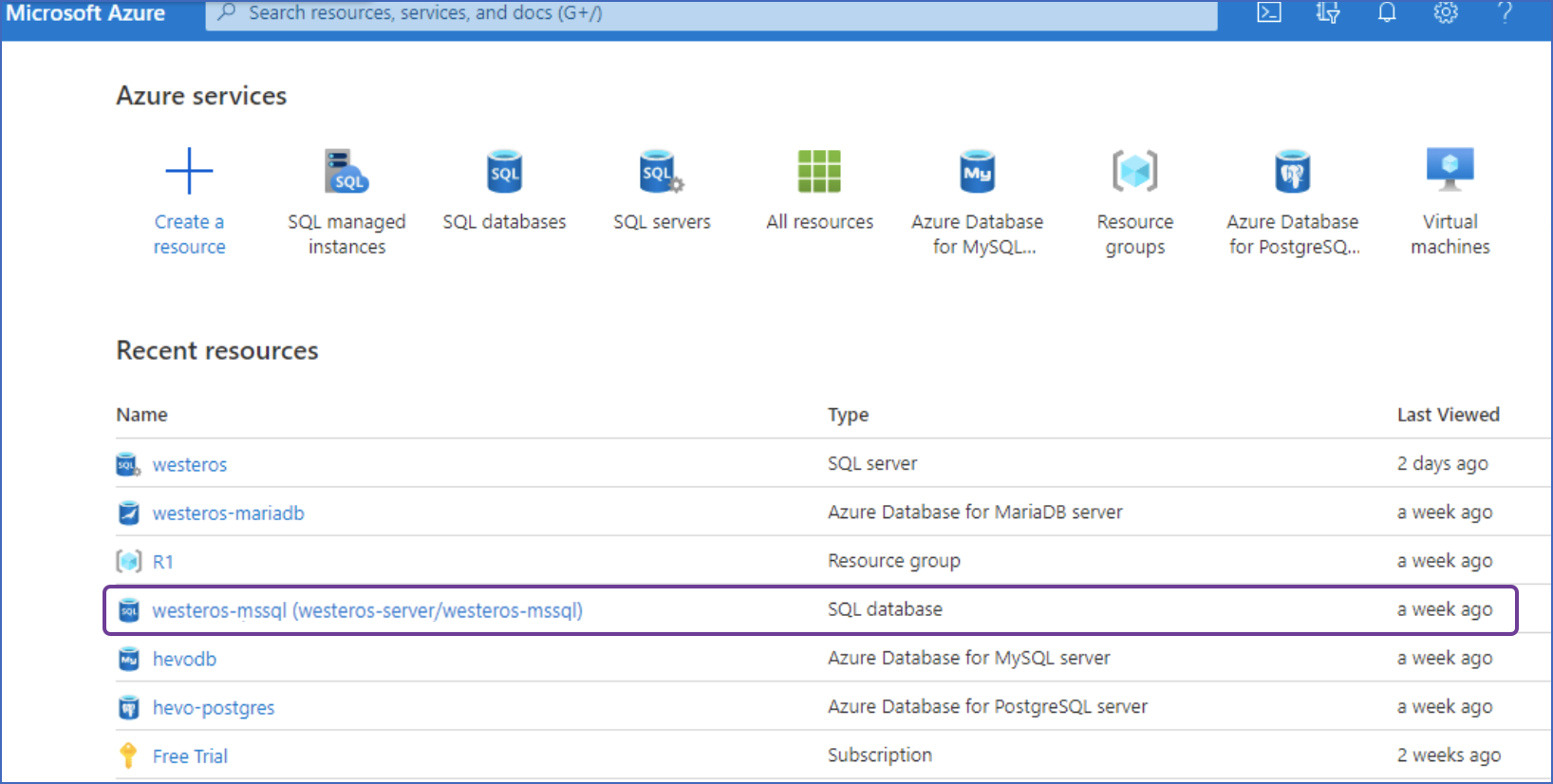
-
In the left navigation pane, under Settings, click Geo-Replication.
-
Under Target regions, select your target region.
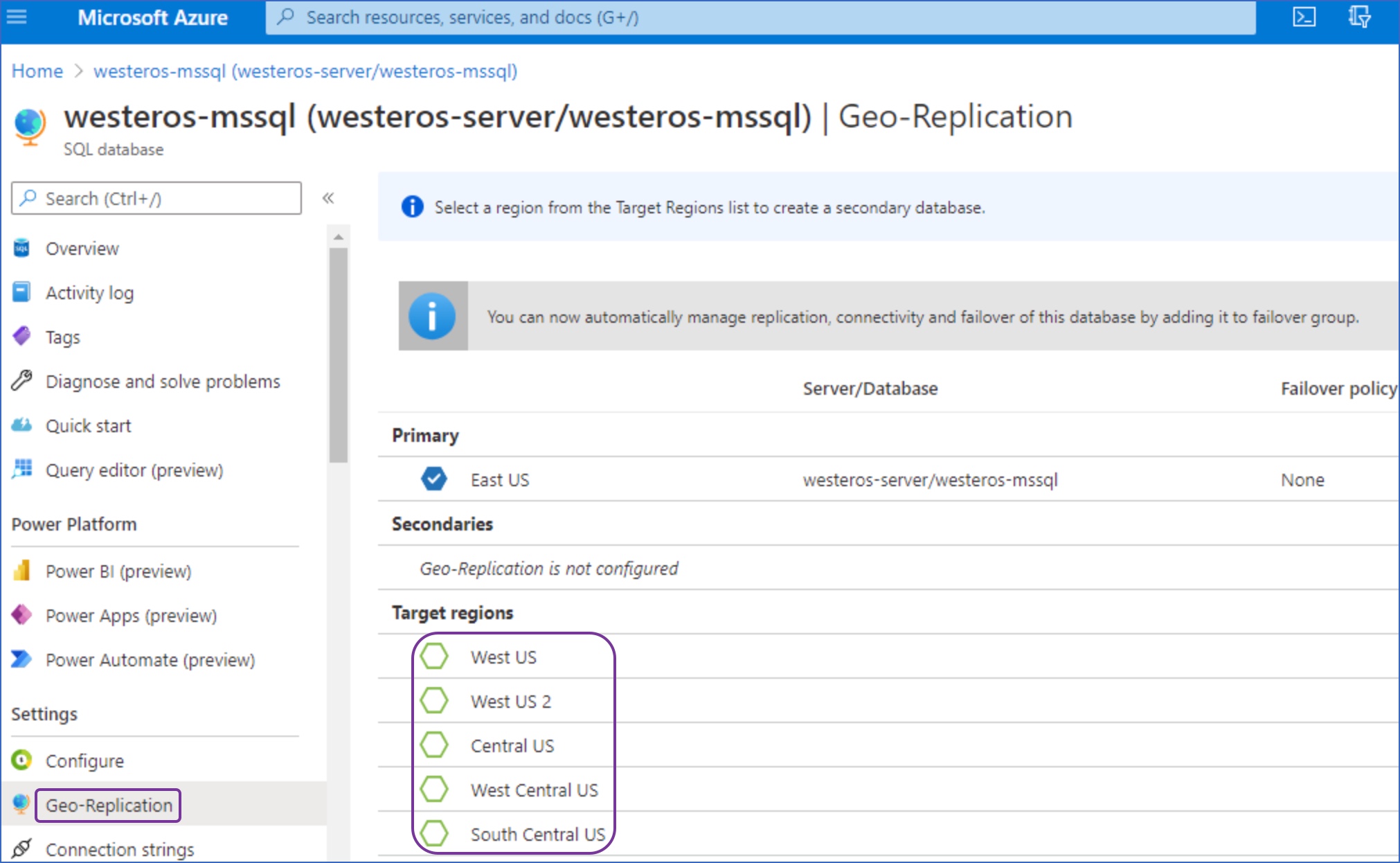
-
In the Create secondary page, specify your Target server, the Pricing tier, and then, click OK to create a secondary database.

A notification is displayed to confirm that the geo-replication database was created successfully.
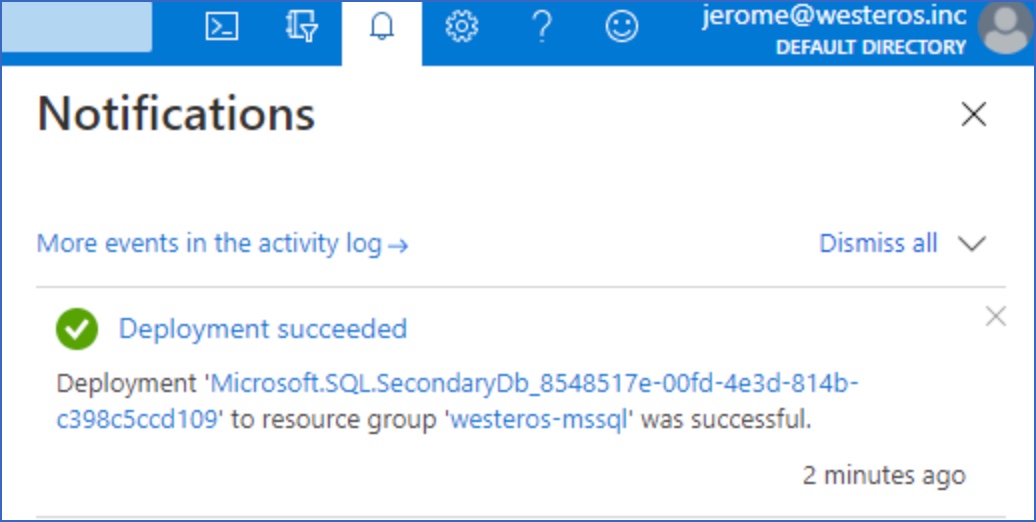
Add Hevo IP Addresses to your Database Allowlist
You must add Hevo’s IP address for your region to the database IP allowlist, enabling Hevo to connect to your Azure SQL Server database. You can do this by creating firewall rules in your Microsoft Azure database settings as follows:
-
Access your Azure MS SQL instance.
-
Under Resources, select the database you want to synchronize with Hevo.

-
In the right pane, click the Set server firewall tab to open the Firewall settings.

-
Create a firewall rule:
-
Specify a Rule name.
-
Specify Hevo’s IP addresses in the Start IP and End IP fields as per your region.
Note: As Hevo has specific IP addresses and not a range, the value in Start IP and End IP fields is the same.
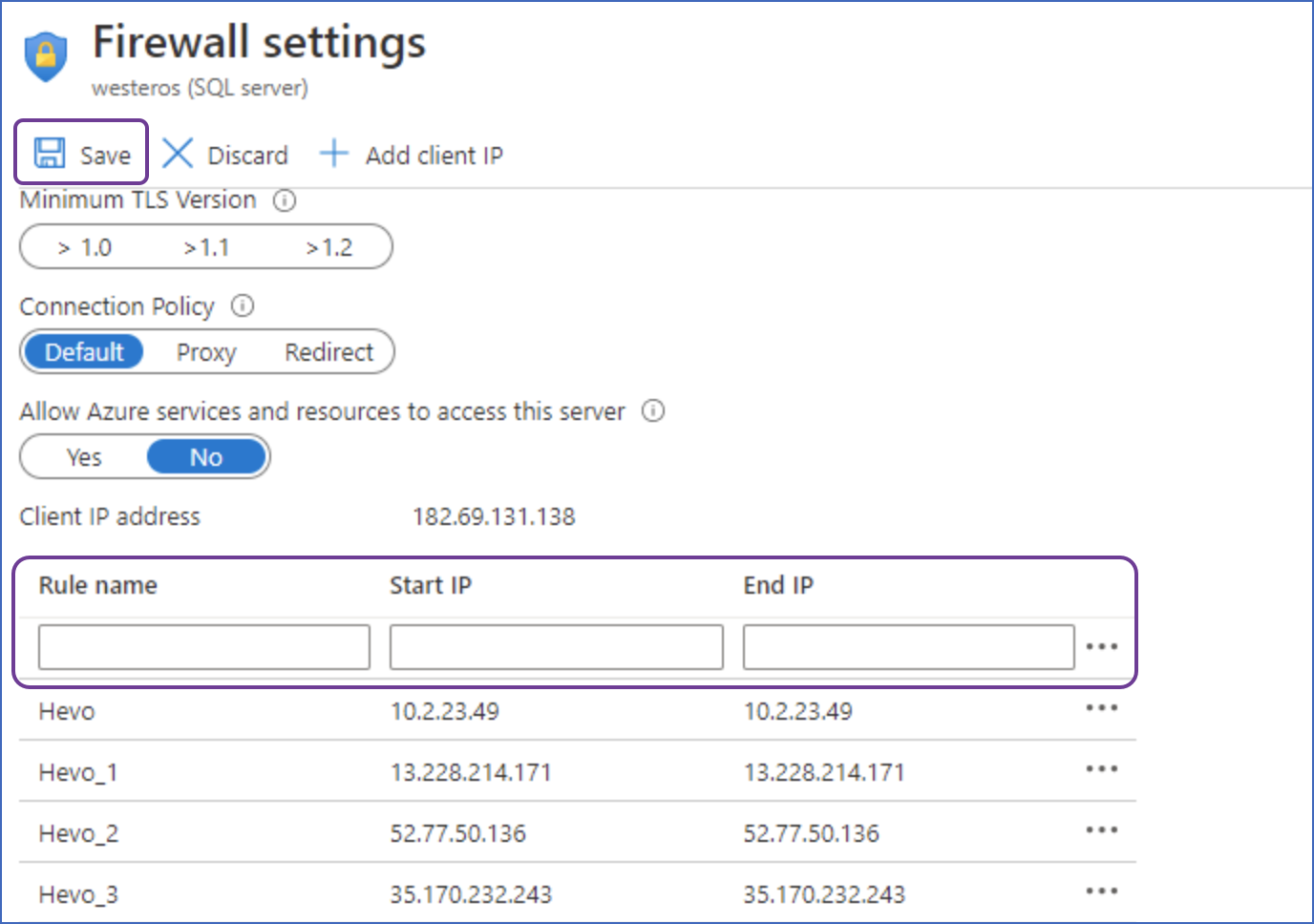
-
Click Save.
-
Repeat this step to add the IP address for each applicable Hevo region.
-
Enable Change Tracking
The Change Tracking mechanism captures changes made to a database. In order to enable, or disable change tracking, the database user must have the ALTER DATABASE privilege.
To enable change tracking, connect your Azure SQL Database in your SQL Client tool, and enter these commands:
-
Enable change tracking at the database level:
ALTER DATABASE [<database>] SET CHANGE_TRACKING = ON; -
Enable change tracking for each table you want to integrate:
ALTER TABLE [<schema>].[<table>] ENABLE CHANGE_TRACKING;
Create a Database User and Grant Privileges
1. Create a database user (optional)
To create a database user, open your Azure MS SQL database in your SQL client tool and enter the following commands:
USE [<database>]; # <database> is the database name
CREATE USER hevo WITH PASSWORD = '<password>';
This creates a contained database user who grants access to the database user on an individual database level instead of the master database level.
2. Grant privileges to the user
The database user specified in the Hevo Pipeline must have the following global privileges:
-
SELECT -
VIEW CHANGE TRACKING
To assign these privileges, connect your Azure SQL Database in your SQL Client tool, and enter these commands:
-
Grant
SELECTprivilege at the table and schema level:GRANT SELECT ON <schema_name>.<table_name> TO <username>; -
Grant
VIEW CHANGE TRACKINGprivilege:GRANT VIEW CHANGE TRACKING ON <schema_name>.<table_name> TO <username>;
Retrieve the Hostname and Port Number (Optional)
Note: The Azure MS SQL hostnames start with your database name and end with windows.net.
For example:
Host : mssql.database.windows.net
Port : 1433
Refer to the steps below to gather the configuration details required to create your Hevo Pipeline:
To retrieve the hostname:
-
Log in to the Microsoft Azure Portal.
-
Under Recent resources, select your SQL database.

-
In the Essentials panel, locate the Server name. Use this as the hostname while creating your Pipeline.

The default port value is 1433.
Specify Azure SQL Server Connection Settings
-
In the Configure your Azure SQL Server Source page, specify the following:
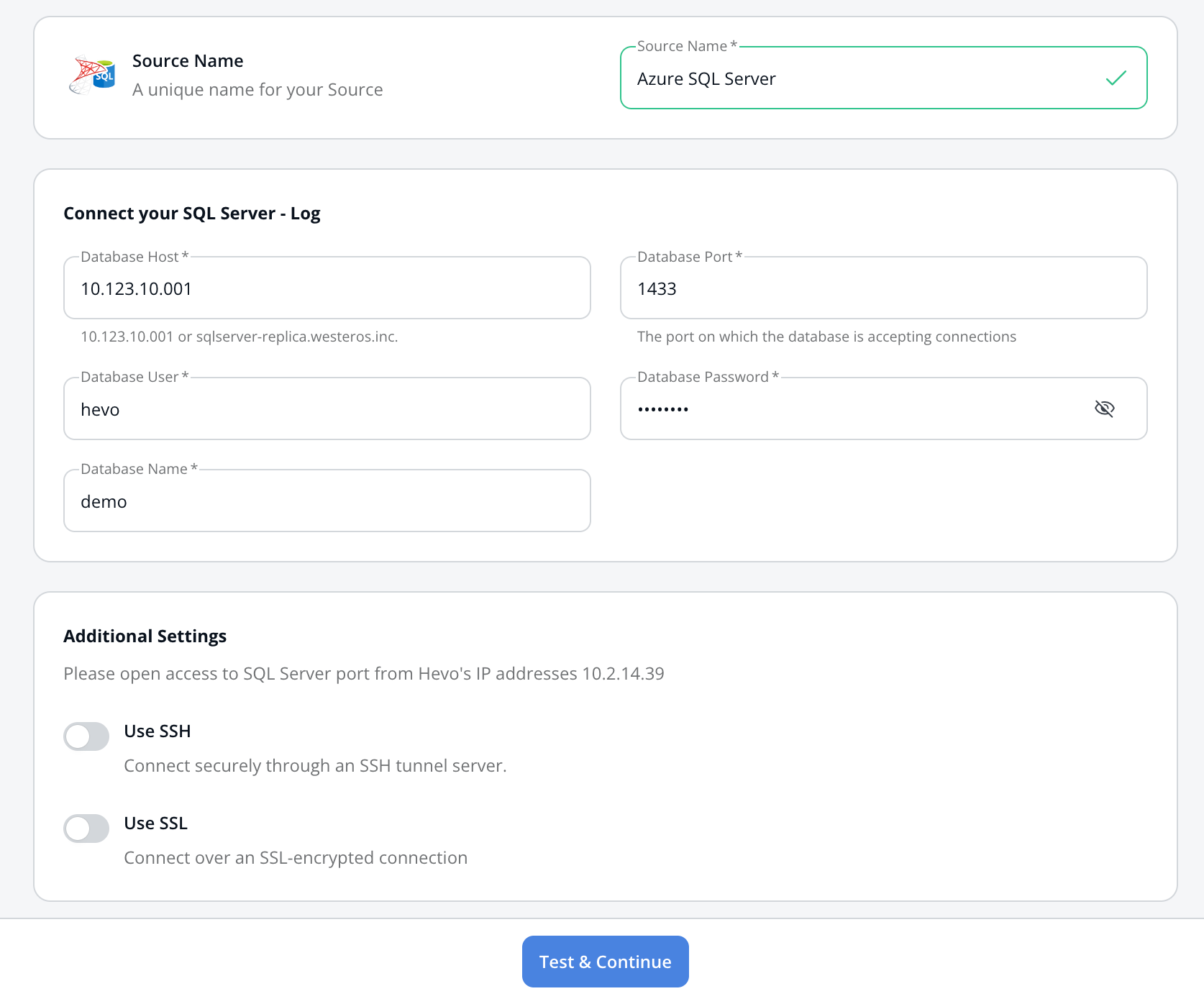
-
- Source Name: A unique name for your Source, not exceeding 50 characters. For example, Azure SQL Server.
-
Database Host: SQL Server host’s IP address or DNS.
Note: For URL-based hostnames, exclude the http:// or https:// part. For example, if the hostname URL is https://mssql.database.windows.net, enter mssql.database.windows.net.
-
Database Port: The port on which your SQL Server is listening for connections. Default value: 1433.
-
Database User: The read-only user who has the permissions to read tables in your database.
-
Database Password: The password for the read-only user.
-
Database Name: The database that you wish to replicate.
-
-
Additional Settings
-
Connect through SSH: Enable this option to connect to Hevo using an SSH tunnel instead of directly connecting your Azure SQL database host to Hevo. This provides an additional level of security to your database by not exposing your Azure SQL Server setup to the public. Read Connecting Through SSH.
If this option is disabled, you must configure your Source to accept connections from Hevo’s IP addresses. -
Use SSL: Enable this option to use an SSL-encrypted connection. Specify the following:
-
CA File: The file containing the SSL server certificate authority (CA).
-
Client Certificate: The client’s public key certificate file.
-
Client Key: The client’s private key file.
-
-
-
Click Test & Continue.