Authentication for GCP-hosted Services (Edge)
Google’s Identity and Access Management (IAM) enables you to provide access to Google Cloud resources, such as Cloud Storage buckets and projects to authorized users (called principals), which may be a user account, a service account (for applications and compute workloads), a Google group, a Google Workspace account, or a Cloud Identity domain. IAM allows you to authorize principals through roles, which are a set of permissions. For example, the Project Creator role contains the resourcemanager.projects.create permission that allows a principal to create a project. The assigned roles can be modified later.
Prerequisites
-
An active Google user account with the required privileges for creating service accounts.
-
The service account has the appropriate role for accessing Google Cloud Storage (GCS) resources. You can assign the Storage Admin role or create a custom role and assign it. If you do not already have a service account, refer to Creating a Google service account for the steps.
Authentication using Google Service Accounts
As a user with the Owner role, you can create service accounts for your team members to access the GCP-hosted services, such as BigQuery. Once you have done this, you must assign the appropriate roles to your service account and download the key file in JSON format.
Creating a Google service account (Optional)
If you have created a service account, skip to the next section to assign it the appropriate roles for accessing your GCP project and, if required, your GCS bucket.
Perform the following steps to create a user-managed service account:
-
Log in to your Google Cloud Platform as a user with the Owner Role.
-
In the left navigation pane, click IAM & Admin, and then click Service Accounts.
-
From the drop-down at the top of the page, select the project in which you want to create the service account.
-
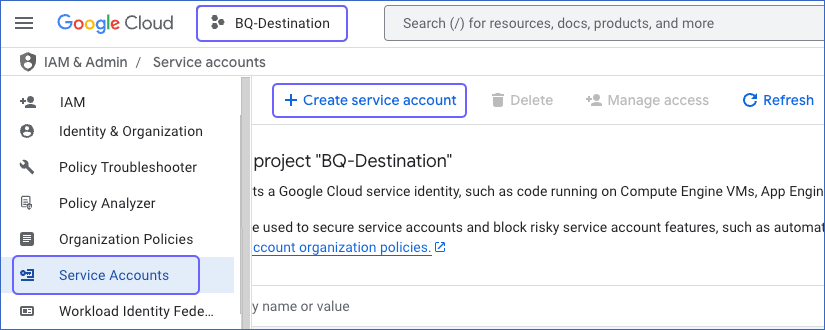
Click + Create service account.
-
On the Create service account page, in the Service account details section, enter a Service account name and a description.
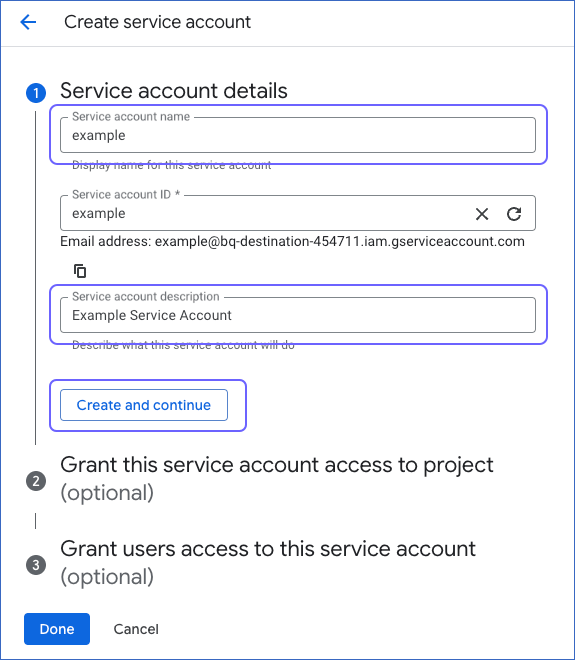
Note: The Service account ID is automatically generated based on the service account name.
-
Click Create and Continue.
-
Click Done and proceed to add roles for your newly created service account.
Assigning roles to a Google service account
To allow your service account to perform tasks on GCP-hosted services, such as BigQuery, you must assign the required roles to it.
You can assign roles to new and existing service accounts. Perform the following steps to do this:
For an existing service account
-
Log in to your GCP console as a user with the Owner role.
-
From the drop-down at the top of the page, select your GCP project.
-
Click IAM & Admin, and then click Service Accounts.
-
On the Service accounts page, hover over the Email of an existing service account and click the Copy (
 )icon to copy and save its email address.
)icon to copy and save its email address.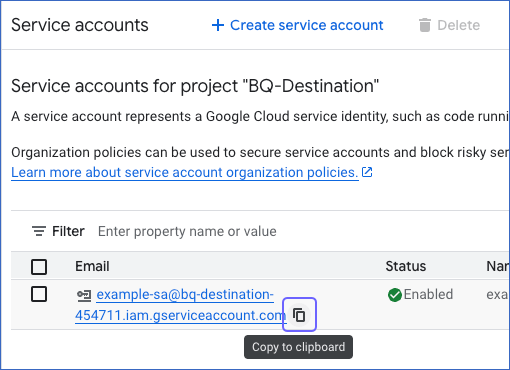
-
In the left navigation pane, click IAM.
-
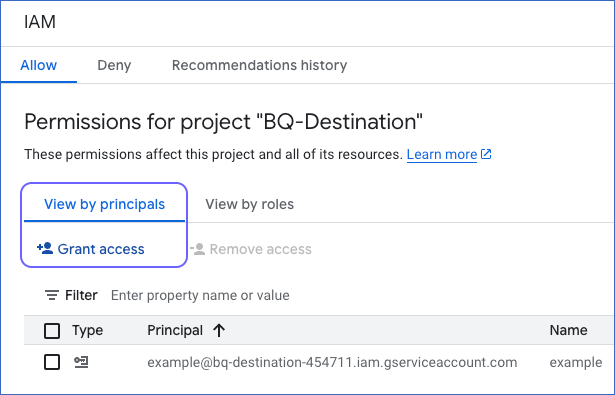
On the IAM page, under the Allow tab, click View by principals and then Grant access.
-
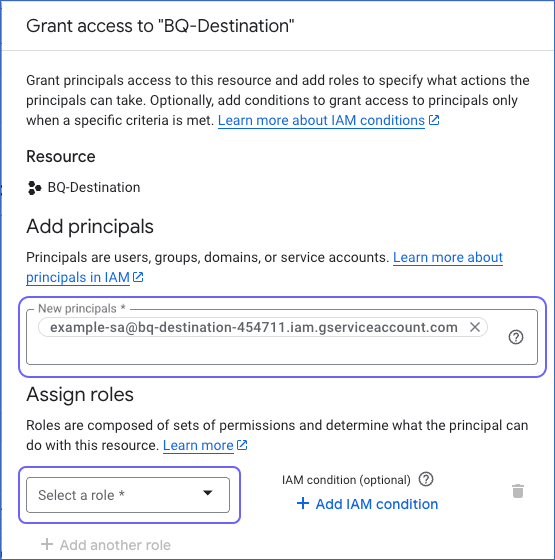
On the Grant access to “<Your GCP Project Name>” page, in the New principals field under Add principals, enter the name of your service account or the email address that you saved in Step 4.
-
Under Assign roles, click Select a role.
-
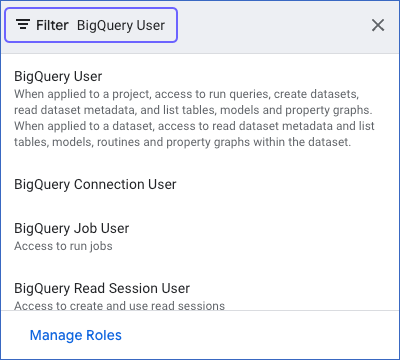
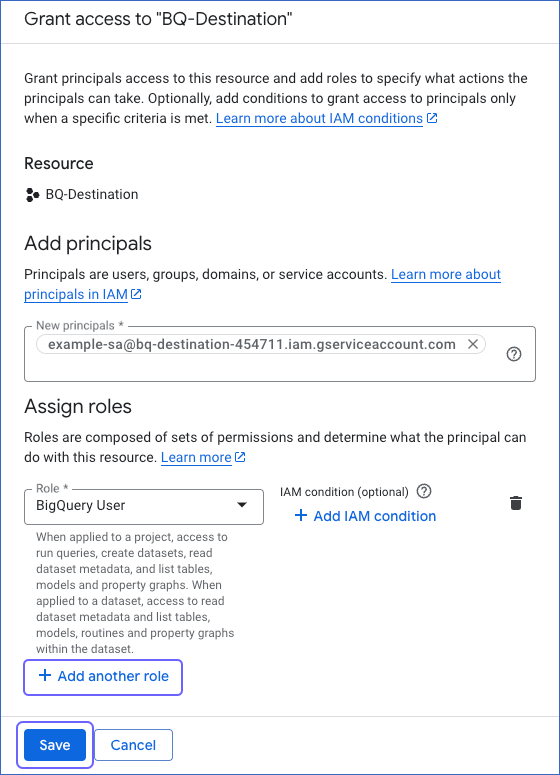
In the Filter field of the window that opens, search for and select the required role to assign it to your service account. For example, BigQuery User.
-
If you want to assign additional roles to your service account, click + Add another role to add a row and repeat the step above.
-
Click Save.
For a newly created account
-
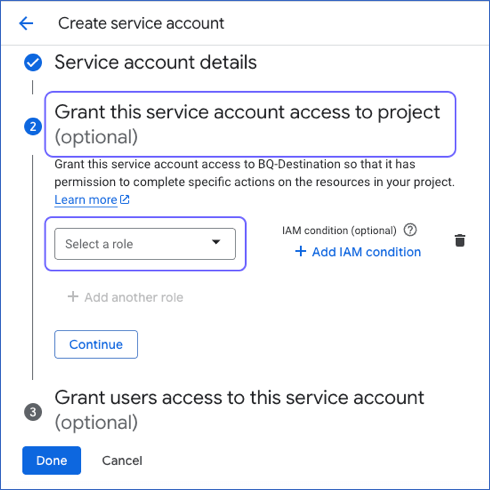
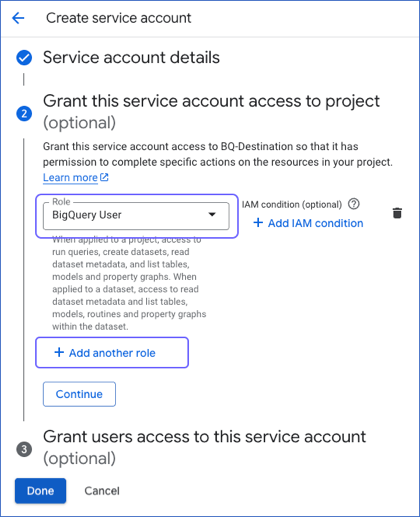
On the Create service account page, continue to the Grant this service account access to project section and click Select a role.
-
In the Filter field of the window that opens, search for and select the required role to assign it to your service account. For example, BigQuery User.

-
If you want to assign additional roles to your service account, click + Add another role to add a row and repeat the step above.
-
Click Done.
Downloading the key file
Service account credentials are a public/private key pair. The public key is stored in Google Cloud, and you must create the private key in JSON format. You need this file to connect your service account to Hevo.
Perform the following steps to create a private key and download it:
-
Log in to your GCP console as a user with the Owner role.
-
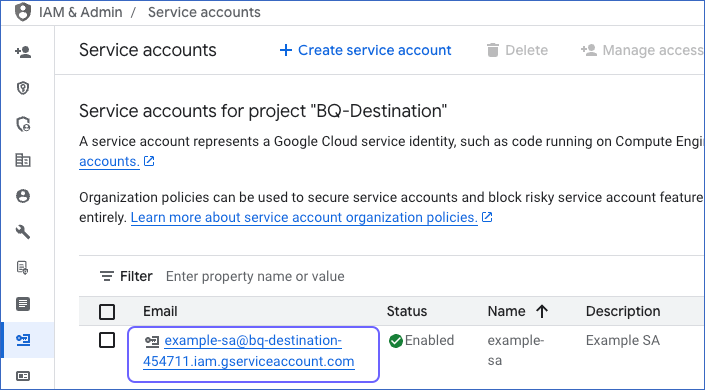
Click IAM & Admin, and then click Service Accounts.
-
On the Service accounts page, click the account for which you want to create the private key.
-
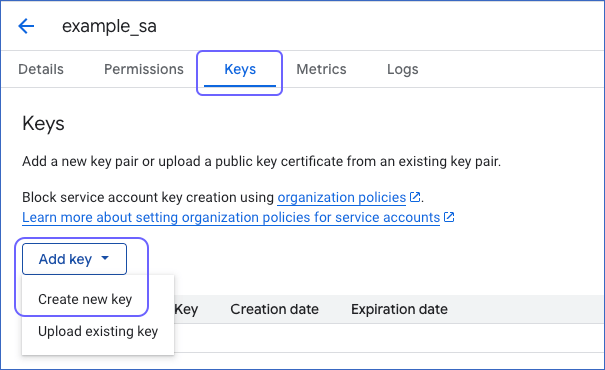
On the <Your service account> page, navigate to the Keys tab.
-
Click Add Key, and then Create new key.
-
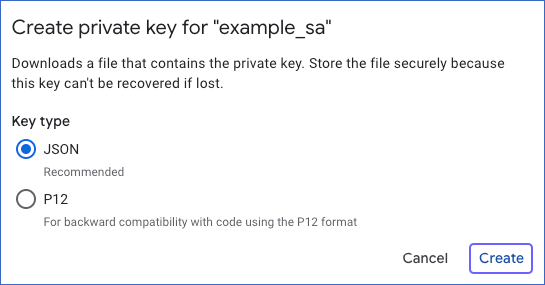
In the Create private key for <your service account> window, select the Key type as JSON and click Create. This creates and downloads the key file. Store it in a secure location.
Note: Hevo supports only JSON format for the key file.
You need to provide this key to allow Hevo to connect to your GCP-hosted service, such as BigQuery, through a service account.